According to this doc-
https://www.retrospect.com/en/support/kb/macos_full_disk_access
We need to give Full Disk Access to both RetrospectInstantScan and Retrospect Client. For this we need to find out the App Identifier and Code Requirements for each.
Retrospect Client application is in /Library/PreferencePanes/Retrospect\ Client.app
RetrospectInstantScan item is in /Library/Application\ Support/Retrospect/RetrospectInstantScan.app
For these examples the first line is the command, the subsequent lines are the response. Base command in red
Retrospect Client App
My_Retrospect_Client:~ admin$ codesign -dv /Library/PreferencePanes/Retrospect\ Client.app
Executable=/Library/PreferencePanes/Retrospect Client.app/Contents/MacOS/Retrospect Client
Identifier=com.retrospect.Retrospect_Client
Format=bundle with Mach-O thin (x86_64)
CodeDirectory v=20500 size=3116 flags=0x10000(runtime) hashes=90+3 location=embedded
Signature size=9014
Timestamp=22 Mar 2022 at 6:56:10 pm
Info.plist entries=25
TeamIdentifier=D6GKVRCPWS
Runtime Version=10.14.0
Sealed Resources version=2 rules=13 files=82
Internal requirements count=1 size=192
My_Retrospect_Client:~ admin$ codesign -dr – /Library/PreferencePanes/Retrospect\ Client.app
Executable=/Library/PreferencePanes/Retrospect Client.app/Contents/MacOS/Retrospect Client
designated => identifier “com.retrospect.Retrospect_Client” and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = D6GKVRCPWS
Retrospect Instant Scan
My_Retrospect_Client:~ admin$ codesign -dv /Library/Application\ Support/Retrospect/RetrospectInstantScan.app
Executable=/Library/Application Support/Retrospect/RetrospectInstantScan.app/Contents/MacOS/RetrospectInstantScan
Identifier=com.retroisa.engine
Format=bundle with Mach-O thin (x86_64)
CodeDirectory v=20500 size=2943 flags=0x10000(runtime) hashes=85+3 location=embedded
Signature size=9013
Timestamp=22 Mar 2022 at 6:56:46 pm
Info.plist entries=22
TeamIdentifier=D6GKVRCPWS
Runtime Version=10.14.0
Sealed Resources version=2 rules=13 files=23
Internal requirements count=1 size=180
My_Retrospect_Client:~ admin$ codesign -dr – /Library/Application\ Support/Retrospect/RetrospectInstantScan.app
Executable=/Library/Application Support/Retrospect/RetrospectInstantScan.app/Contents/MacOS/RetrospectInstantScan
designated => identifier “com.retroisa.engine” and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = D6GKVRCPWS
Putting it all together
So we can see that we need these 4 bits of information, and each item also needs 2 sets of permissions. Here is a screenshot of what it looks like in Mosyle under Management Profiles/ Security & Privacy/ Privacy
**Warning- you can copy and paste the text above, but the pics are slightly wrong ‘com.retrospect.Retrospect’ is now ‘com.retrospect.Retrospect_Client’
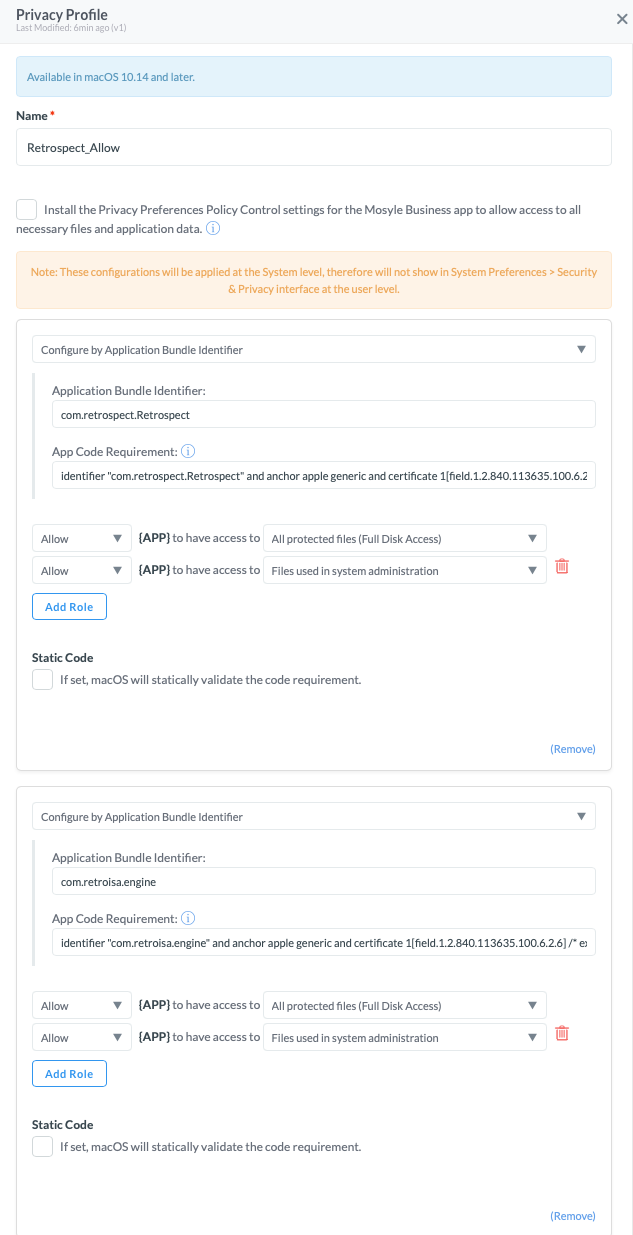
You can also simply allow the Team Identifier, but this is perhaps a more secure method.
Thanks to Addigy for providing the documentation, fake thanks to Retrospect and Mosyle for not documenting this.