The Short Version
TL;DR – add a DNS server that’s not on either network and is publicly accessible, and possibly also a static route. Also maybe set the VPN profile to a higher priority…
**I’ve thought over this and of course the solution seems obvious. But the doc from Ubiquiti makes it sound difficult, so not really sure what is going on…
The Long Version
Been having a lot of trouble with Unifi VPN lately. People can connect to the VPN, and get access to their Server, but they can’t browse the internet properly.
This is pretty much by design, as you don’t really want your shiny network to have a node that isn’t exposed to your firewall. So you’d want people connecting to your VPN to NOT be allowed to get malware from the internet at the same time.
Unfortunately we live in the real world and for some reason clients don’t want to have 2 computers running just so they can do both things…
Digging deeper, it seems their internet connection is working fine because they can ping a host like 8.8.8.8
But they can’t resolve anything on the big bad ‘net.
Without going into too much detail, it seems to be because of this-
https://help.ui.com/hc/en-us/articles/115005445768-UniFi-USG-UDM-Configuring-L2TP-Remote-Access-VPN
If you are intending to use a ‘split tunneling’ setup and disable the gateway option on your clients, then you will need to manually add the necessary routes to the routing tables on the clients. The L2TP VPN is unable to push any routes to the client devices.
It looks like Ubiquiti are trying to enforce their ‘workaround’ in the background because it does something incredibly stupid.
Example
Office IP Range 192.168.1.1/24
Server 192.168.1.100
UDM Pro 192.168.1.1
VPN Range 192.168.55.1-254
Your Local computer 192.168.20.30
You connect to the VPN and are given the IP address 192.168.20.22
Then you can connect to the Server at 192.168.1.100, but you can’t browse to FreeMoviesAndMalware.com
and you can’t do a DNS lookup for it, but you can ping it (and any other host) if you know it’s IP.
Forcibly setting the Office networks DNS to the VPN clients doesn’t work, and neither does setting ANY DNS server on the local client manually.
Here’s what I think is happening- Unifi is setting up a static route that instead of targeting the VPN network, targets a much larger network range. They actually say in their ‘workaround’ doc to do exactly this.
It seems pretty likely that
When you set the DNS to be the office network DNS, the routing tables force the traffic back into the office network- result- no browsing outside resources
When you set the local DNS to be ANYTHING, the routing tables force the traffic back into the office network- result- no browsing outside resources
The Solution
I was able to get around this for one client by setting a VPN DHCP range that was outside the range that Unifi tried to claim, and thought no more of it. But it came up again this week so I was forced to find a ‘real’ solution.
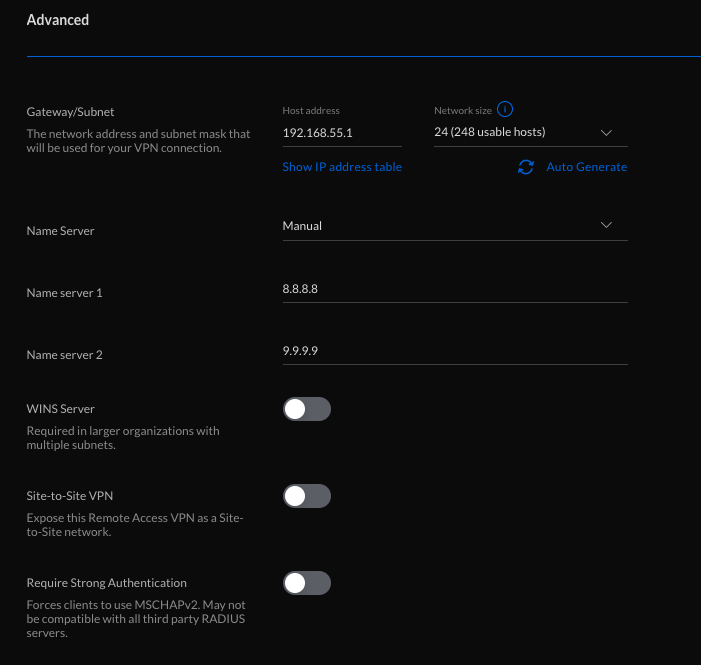
Set the DNS server that the VPN clients are forced to use to a DNS server that is public, and outside both networks. So any combination of 8.8.8.8, 8.8.4.4, 1.1.1.1, 9.9.9.9 or 208.67.222.222 and 208.67.220.220 should work…
This is in Networks/ Client VPN/ Advanced
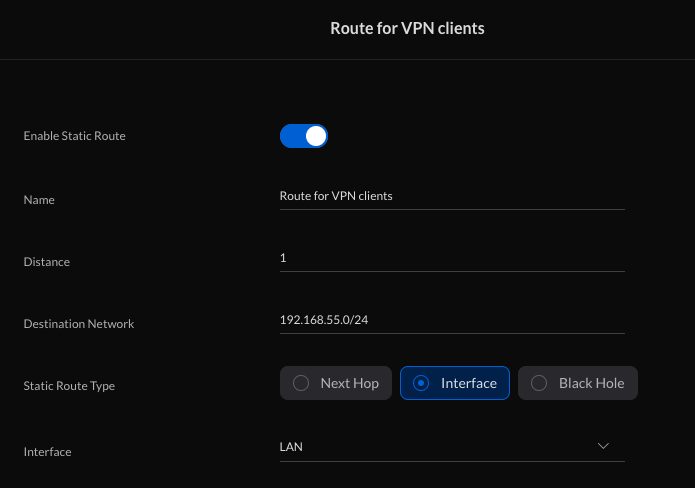
I think you should also have a static route set up to force traffic to the office network, but I guess that just ‘good behaviour’ rather than a necessity.
This is in Advanced Features/ Advanced Gateway Settings/ Static Routes
I hope one day to have the time to prove this, but for now let’s say it works
Addendum
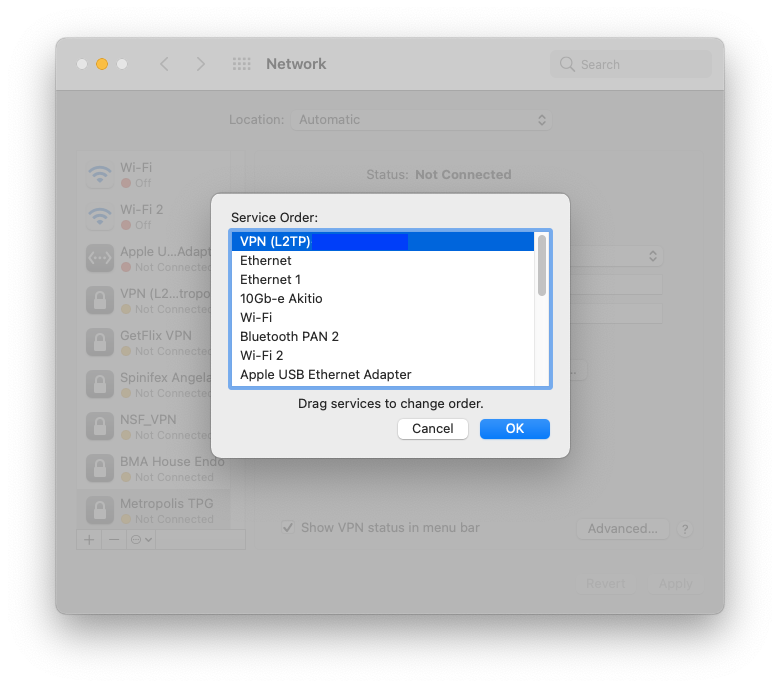
One client had issues with this as set up- we had to go to System Preferences/ Network and set the VPN to the highest priority to get it’s routing rules respected.